Create Connect Server
Objective
We could use our domain controller for the AD Connect synchronization server, but this is a bad idea. There's typically multiple (primary, secondar, maybe more) domain controllers in an Active Directory environment. We are only allowed to have one active/hot AD Connect synchronization server in our environment. What happens if the domain controller where the the synchronization tool is installed fails? We would lose synchronization capabilities.
Let's create a standalone AD Connect synchronization server.
Create the Server in Azure
If you are not currently at dashboard within the Azure portal, go ahead and close all blades.
On the left menu, you should see Virtual machines ![]() . Click it.
. Click it.
-
In the actions section of the virtual machines blade, click on
 .
. -
In the Search Compute search box, type in Windows Server 2016 Datacenter. Press Enter.
-
In the returned results, choose the option that simply reads
 .
. -
In the next blade, make sure Resource Manager is selected. Then, click Create.
-
There are 4 sections to configure the virtual machine.
-
Basics
- Name: ad-connect
- VM disk type: SSD
- Username: cloudadmin
- Password: Pass@word1234
- Confirm Password: <same as above>
- Subscription: Free Trial
- Resource Group: Use existing - <use the same resource group created by the CLI>
- Location: <use the same location you chose in the CLI>
- Save money: No
-
Size
- DS1_V2
-
Settings
- Use managed disks: No
- Storage account: <use the same storage account created by the CLI> (e.g. azwdata###)
- Network: vnet
- Subnet: default (10.3.1.0/24)
- Public IP address: (click on it & Create new)
- Name: connect-ip
- Assignment: Static
- Network security group (firewall): None
- Extensions: None
- Availability set: None
- Boot diagnostics: Enabled
- Guest OS diagnostics: Disabled
- Diagnostics storage account: <use the same storage account created by the CLI> (e.g. azwdiags###)
-
Summary (just click OK to continue)
-
The machine we chose for this workshop is relatively small. After all, we only have 4 identities that we'll be synchronizing with Azure AD. If this was a production environment we would have to take into consideration that password sync's occur approximately every 2 minutes while full synchronization happens every 15-30 minutes. For production, we would need to choose a machine that is more capable of handling the workload.
Keep in mind, that we are treating Azure like our on-premises datacenter. In reality, we would have simply created a new VM in our on-premises hypervisor (Hyper-V, VMware, etc.)
Add Machine to Domain
We need to add the new machine to our Active Directory domain. AD Connect must be installed on an AD-joined machine.
Set the Private IP as Static
Before we add the machine to the domain, we need to set the private IP to static so that Azure's DHCP server doesn't reassign the IP to another machine.
-
If you are not viewing the details on the newly created machine, click on the Virtual machines
 menu item, then click on the ad-connect machine in the list.
menu item, then click on the ad-connect machine in the list. -
Once you've clicked on the ad-connect machine and are viewing the machine's Overview blade, choose Network interfaces
 .
. -
In the resulting list of network interfaces, choose the single NIC that is listed (e.g. ad-connectXXX).
-
On the network interface menu, click on IP configurations
 .
. -
The resulting list should only contain a single configuration - ipconfig1. You'll notice that under the heading PRIVATE IP ADDRESS, the configuration is listed as Dynamic. Click on this configuration.
-
In the settings for the configuration, under Private IP address settings, change the Assignment to Static. (The IP address should be 10.3.1.6. If it is not, update it, as well.)
-
Click Save.
You can now close the two blades (e.g. ad-connectXXX, network interface) to arrive at the main Network interfaces ![]() blade for the ad-connect virtual machine.
blade for the ad-connect virtual machine.
Connect to the Machine via Remote Desktop
To connect to the machine remotely, we need to download the Remote Desktop Protocol (RDP) profile.
-
Click on the Overview
 to return to the general information for the ad-connect virtual machine.
to return to the general information for the ad-connect virtual machine. -
In the Actions section, click on Connect
 . This will download the RDP profile to your machine.
. This will download the RDP profile to your machine. -
Open the profile and accept any warnings.
-
For the username, enter \cloudadmin (with the backslash). And, for the password, enter Pass@word1234. Click OK.
-
Again, accept any warnings.
Add the Machine to the Domain
When you initially connect to the machine, you will see the Server Manager dashboard.
We've already set the IP on the network interface card (NIC) to be static in Azure. Technically speaking, we've created a reservation in Azure's DHCP server for the NIC in our virtual network. However, before we add the machine to the domain, it is best if we set the IP as static within Windows Server's TCP/IP configuration.
-
In the left menu of Server Manager, click on Local Server.
-
In the resulting page, you'll see a couple of sections. The first section is labeled Properties. Properties has two columns. Half-way down the left column, you'll see Ethernet followed by a number. Beside this, you will see in blue IPv4 address assigned by DHCP, IPv6 enabled. Click on this.
-
This will open the Network Connections window. Right-click on the single listed adapter and click on Properties in the context menu.
-
In the Properties window for the NIC, scroll down until you see Internet Protocol Version 4 (TCP/IPv4). Highlight it, then click Properties.
-
Enter the values as you see them below.
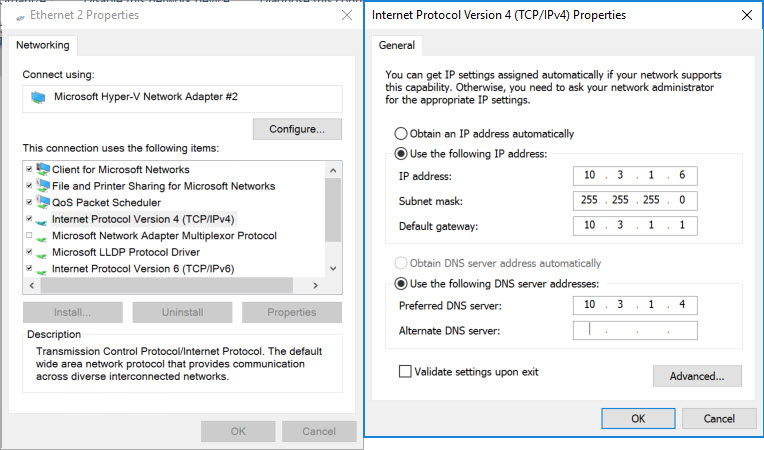
-
Click OK, the Close. NOTE: Clicking Close will cause a brief interruption in your connectivity. That's okay. The connection should be re-established within a couple of seconds.
-
Once the connection has been re-established, you can close the Network Connections window.
-
Back in the Properties section, in the half-way down the right column, you will see IE Enhanced Security Configuration. To the right of that in blue, you probably see On. Click on it.
-
In the Internet Explorer Enhanced Security Configuration dialog, choose Off for both, Administrators and Users. Then, click OK.
-
Once more, in the Properties section, the second item listed in the left column reads Workgroup. To the right of that, you will see in blue WORKGROUP. Click on it.
-
In the System Properties dialog, half-way down, click on the Change button.
-
In the resulting Computer Name/Domain Changes dialog:
- Leave the Computer name as it is (e.g. ad-connect).
- Under Member of, change the selection to Domain and enter the domain name you entered earlier in the CLI (e.g. mycompany.local).
- Click OK.
- For the username and password enter your Domain Admin username and Domain Admin Password, respectively, as reported previously by the CLI.
- Click OK.
If all goes well, you should be added to the virtual datacenter domain and receive a message stating as much. To complete this will require a reboot, thus disconnecting you from your remote session.